Patch management is a crucial yet often underestimated component in the complex landscape of cybersecurity protocols. This vital process involves timely distribution and installation of software updates, essential for bolstering an organization’s defense mechanisms against cyberattacks. Diligently managing patches forms a robust barrier against exploiting known security vulnerabilities, thereby securing networks from potential breaches.
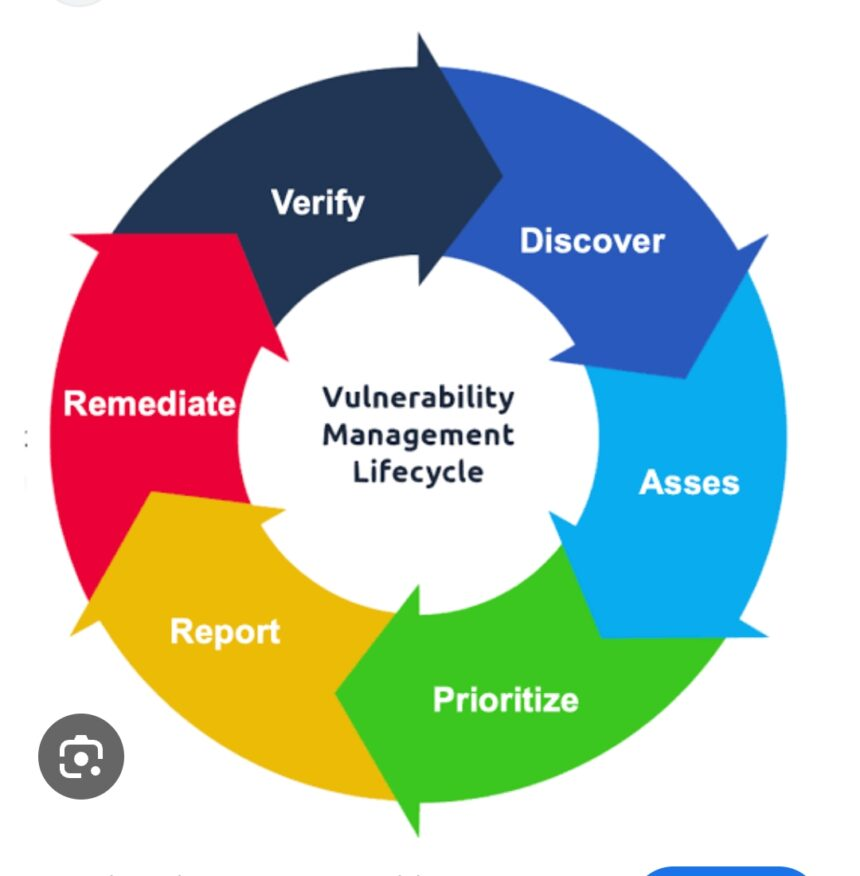
Understanding Patch Management in the Vulnerability Lifecycle
Patch management plays a pivotal role throughout an organization’s vulnerability lifecycle. It begins with detecting vulnerabilities and extends to deploying patches designed to mitigate them. This meticulous process requires coordinated efforts across IT systems and departments to ensure infrastructure security and operational continuity. Rapid and accurate execution of patch management is imperative to maintain effective cyber resilience against evolving threats.
The Impact of Neglected Patches
Even a single unpatched system can serve as a gateway to a significant security breach with widespread repercussions. Delayed responses to patch releases significantly increase the risk of security breaches. Such oversights in patch management can trigger a chain reaction, leading not only to isolated incidents but also mass exploitation of network vulnerabilities. Beyond digital damage, these lapses can undermine an organization’s integrity, legal standing, and stakeholder trust.
Strategies for Effective Patch Management
Successful patch management employs complex, multifaceted strategies. Prioritizing patch deployment based on threat severity and system criticality is crucial. A phased rollout, starting with controlled environments before wider deployment, minimizes risks of unintended system disruptions. Incorporating feedback mechanisms enables organizations to refine patch management processes with each deployment cycle.
Automation in Patch Management
Automation is increasingly integral to modern patch management strategies. Advanced IT tools automate routine aspects of patch deployment, enhancing efficiency and reliability. Automated systems can detect patch requirements, test compatibility, and deploy updates across diverse environments with minimal human oversight. This shift frees up IT resources for strategic initiatives while ensuring systems remain updated against emerging threats.
Best Practices in Patch Management
Adherence to best practices strengthens an organization’s IT security posture. Regular vulnerability assessments pinpoint critical areas needing immediate attention. Maintaining comprehensive inventories of systems and applications ensures every asset is accounted for and secured. Clear policies for system backups before patch application mitigate risks of data loss due to patch-related failures. Educating employees on the importance of updates reduces human errors that could compromise security.
Patch Management’s Role in Security Posture
A robust patch management program underscores an organization’s commitment to proactive cybersecurity. It anticipates and mitigates threats before they escalate, demonstrating a strong security culture to stakeholders and regulatory bodies alike. Effective patch management not only safeguards against cyber threats but also facilitates compliance with regulatory frameworks, ensuring business operations remain resilient and secure.
Conclusion
In the realm of vulnerability management, patch management stands as a cornerstone of cybersecurity defense. Despite its challenges, the cost of neglecting this critical aspect far exceeds the investment in its meticulous management. By embracing best practices, leveraging automation, and fostering a culture of security awareness, organizations can effectively navigate the complexities of patch management and safeguard against the persistent threat of cyberattacks.
Leave a Reply